October is National Cybersecurity Awareness Month and UAH OIT is using it to reinforce our shared responsibility to keep the UAH information systems and data safe for everyone.
Phishing is any attempt to scam a user into revealing sensitive information such as bank details, passwords, or credit card numbers, by sending malicious links to the user. These attempts commonly appear as links in email but can also be sent via SMS (text message), chat message, or appear on web pages as well. A similar tactic to phishing is what’s known as "pretexting" where the attacker tries to convince a victim to give up valuable information or access to a service or system. The distinguishing feature of this kind of attack is that the attacker comes up with a story - or pretext — in order to fool the victim.
According to the 2021 Verizon Data Breach Investigation Report, phishing attacks were the most common attack vectors in data breaches in the last year, focusing on COVID-19 topics like vaccines and quarantines, most commonly securing login credentials like usernames and passwords. According to that same report, 43% of data breaches in 2020 began with a phishing or pretexting attempt.
What is Pretexting? Watch: KnowBe4 Pretexting - Fake IT Password Break-In
Because regular data breaches occur at various companies, medical facilities, and social media sites, phishing attacks are becoming increasingly sophisticated, targeted, and personal. Where attackers used to send out hundreds of thousands of phishing attempts without regard to whether they made sense, now they will send phishing attempts to people using data obtained by various data breaches. New phishing attempts may know where you shop, what you purchased and any data you’ve shared on social media. This personal information increases the success rate of the phishing attempt so it's worth it to the attackers to collect this data and use it to attempt to phish users.
What can you do?
While Google has good protection measures in place, they cannot stop 100% of phishing attempts so we need everyone to be vigilant and watch for phishing attempts in their email.
In order to assist you with identifying potential phishing emails, UAH clearly labels any email originating from outside the UAH.edu domain with an [External] label that shows up on the web interface.
The first thing you should do is be wary of and carefully scrutinize any message that is attempting to entice you to take action immediately. The attacker is attempting to get you to make a snap decision without considering the implications or weighing the potential security issues. Examples of this include (but certainly aren't limited to): a bill from a service provider like phone company, doctor, or UAH that includes a bill for an exorbitant amount and a link for you to either pay the bill or ask for clarification; a text message from UAH management "updating the COVID policy" but the link takes you to a link shortener like bit.ly, ow.ly, or goo.gl rather than the actual company’s site.
Phishing attackers will often include official logos from companies in their emails or messages. Just because it has a Microsoft or Verizon logo doesn't mean it came from that company.
When you receive an email apparently from a company you've done business with and asking you to click a link, you should open your web browser and go to that company's website or contact the company's customer service department to ask about the contents of the email.
As a reminder, UAH will never ask for your password to fix an issue.
If you do receive a phishing email and you have not replied to the email (or clicked on any links in the message) then no further action should be necessary. If you have clicked on a link and provided your password, we advise that you change your UAH password immediately:
- Visit oitportal.uah.edu
- Login
- Change your password on the My Password(s) tab
Finally, if you receive a message you believe to be phishing or spam, we advise you to click the "Report Spam" option for the message in Gmail (or other email client if the option is available). This helps Google learn that the sender is generating these messages and will flag further messages from that user as spam.
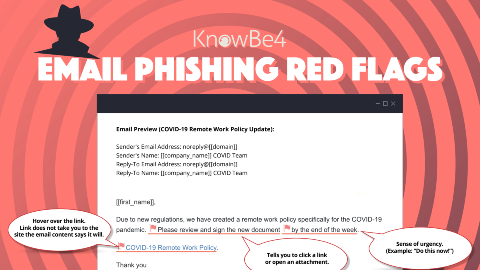
How well can you recognize phishing emails? Take a look at these Phishing Red Flags to help all of us #BeCyberSmart.
By following these simple steps, you can help keep your, your fellow students' and UAH’s data safe and secure.
For questions or more information, contact ciso@uah.edu